British Government Responds To Media Claims Sellafield Nuclear Site Had Been Cyber-Attacked
The Guardian reported that the British nuclear site was infected by sleeper malware that had been detected as far back as 2015.
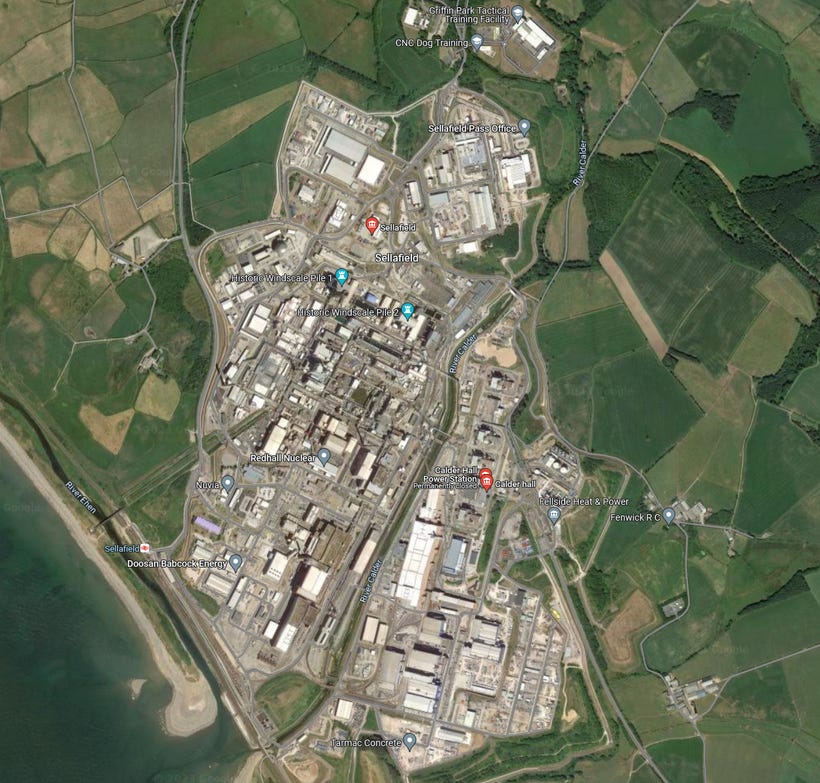
LONDON - After The Guardian news outlet released an article claiming that the Sellafield nuclear site had been cyber-attacked by state actors mostly linked to Russia and China, the British government released a statement saying that the claims were false and that they have no records or evidence to suggest that Sellafield Ltd networks had been attacked by state-actors "in the way described by the Guardian".
The statement added that the agency is "confident that no such malware exists" on their system.
The Guardian report claimed that the site was infected by sleeper malware that had been detected as far back as 2015, but that the authorities don't know when it was first compromised, and it is not known if the malware has been eradicated.
"It may mean some of Sellafield’s most sensitive activities, such as moving radioactive waste, monitoring for leaks of dangerous material, and checking for fires, have been compromised," the report stated.
"The astonishing disclosure and its potential effects have been consistently covered up by senior staff at the vast nuclear waste and decommissioning site," The Guardian report said.
Not subscribed and want to dig deeper? Consider paid access for more information, full conversation transcripts and statements, research screenshots, images, documents videos, notes, and data. More updates may be posted below in the paid section.
British Government: No Such Malware Exists On Our System, This Was Confirmed To The Guardian Well In Advance:
Keep reading with a 7-day free trial
Subscribe to The Standeford Journal - News, Intel Analysis to keep reading this post and get 7 days of free access to the full post archives.